What is internal security?
1. Internal security refers to the measures and actions taken by a government to maintain law and order, protect its citizens, and safeguard its sovereignty within its own borders. It is the responsibility of the government to ensure that the country’s citizens, institutions, infrastructure, and resources are protected from threats such as terrorism, insurgency, organized crime, cyber-attacks, and communal violence.
2. The earliest treatise of statecraft – Arthashastra by Kautilya – had references to management of security of state from internal as well as external threats.
Role of media and social media
1. With the rise of digital revolution, the role of media and social media has increased exponentially as source of collection and dissemination of information.
2. According to Digital News Report 2022, from Reuters Institute for the Study of Journalism, 63% Indian respondents used social media as their primary source of news.
3. Media includes various news channels on televisions, FM radio stations etc. where as social media includes multiple social networking sites like facebook, Whatsapp, twitter etc.
4. The media and social media are proving to be a double edged sword in present world i.e it they are promoting society welfare as well as creating challenges for the society and nation.
Significance of media and social media
1. Information dissemination: Social media platforms such as Facebook and Twitter have become a primary source of news for many people worldwide. For example, during the Arab Spring protests in 2011, social media played a significant role in disseminating information and organizing demonstrations.
2. Connectivity: Social media platforms have made it possible for people to connect with others around the world. According to Statista, as of January 2022, there were 4.89 billion active social media users worldwide. Social media platforms such as Facebook and Instagram have become a primary means of communication and social interaction for many people worldwide.
3. Influencing public opinion: Social media platforms can play a significant role in shaping public opinion. Social media has also been used to spread positive messages and mobilize people to support social and political causes. For example, the #MeToo movement gained momentum on social media platforms and led to significant social and cultural changes.
4. Marketing and advertising: According to a 2021 survey by eMarketer, global social media ad spending is projected to reach $110 billion in 2022. Social media platforms allow businesses to reach a vast audience and engage with their customers in new and innovative ways. For example, Instagram has become a popular platform for influencer marketing, with brands paying social media influencers to promote their products to their followers.
5. Accountability: Media and social media have the power to hold individuals and organizations accountable for their actions. For example, the 2012 India against corruption campaign was heavily supported by multiple media houses leading to generation of huge support for the campaign and its success.
Challenges
1. Cyber Terrorism: Terrorists today use social media as a practical alternative to disrupt the functioning of nations and other business activities due to its potential for significant damage. Terrorist groups have become particularly fond of Skype, a chat service that supports both voice and video. The insurgent and extremist groups can communicate with members and supporters worldwide through chat rooms and electronic forums, recruit new followers, and share information without fear of being identified by authorities.
2. Dissemination of fake news and misinformation: Social media platforms such as WhatsApp, Facebook, and Twitter have been used to spread fake news and misinformation that can create social unrest and harm national security. For example, in 2018, false rumors spread on social media about child kidnappings led to mob violence and lynching incidents in several Indian states.
3. Encouraging radicalization: Some media outlets and social media platforms have provided a platform for extremist groups or individuals who advocate violence or other forms of radicalization. This can increase the risk of terrorist attacks and other security threats within India. For example, ISIS used social media to recruit Indian youths and inspire them to carry out terrorist attacks.
4. Reporting sensitive information: Media outlets may report sensitive information related to national security, such as military strategies, troop movements, or intelligence operations. This can compromise the safety of the military personnel involved and undermine the effectiveness of these operations.
5. Sensationalism: Some media outlets may exaggerate or sensationalize security threats to attract viewers or readers, creating an atmosphere of panic and fear. This can lead to overreactions and inappropriate responses by the government or public, which can harm national security.
6. Cybersecurity threats: India faces cybersecurity threats from various state and non-state actors, including hostile foreign governments, terrorist groups, and cybercriminals. Social media platforms and other online tools can be used to launch cyber attacks on Indian infrastructure, steal sensitive data, and spread propaganda.
Issues in regulating media and social media
1. Regulation of any media content is seen as gagging or censorship by the media activists. It makes difficult for the government to balance national security and media rights.
2. Social media go beyond the traditional mechanisms of censorship and regulation. For example, IT Act, 2000 doesn’t mention social media sites, you tube channels, reels which have now become a major type of media information dissemination.
3. National governments face challenges as a result of social media’s transnational nature. Social media’s lack of local data storage raises jurisdictional issues when dealing with crimes via social media.
4. Private businesses own a significant portion of the infrastructure because they consider security measures and routine auditing to be unnecessary expenses, making it difficult to safeguard individuals from social media-related crimes.
Steps that can be taken
1. Self-regulation: Due to the fact that excessive government regulation can be detrimental, the media itself ought to discover ways to self-regulate.
2. Penalizing powers to PCI: In order for the PCI to better manage the media in terms of professionalism and accuracy of information, it may be granted penalizing authority. Also, the News Broadcasting Standards Association ought to take steps to limit sensationalism and TRP lust in news channels.
3. Formulating a national security policy: putting into place the blueprint for a national social media policy in order to keep an eye out for security threats on social media and regulate it.
4. Involving the major players in social media: in the fight against the use of social media for criminal and anti-national activities.
5. Cyber intelligence: must be used to improve cybersecurity. Utilizing big data analysis and artificial intelligence to track online criminal activity.
6. Fixing accountability of social media platforms: Traffic to social media platforms is beneficial. They must be subject to regulatory regimes and held accountable to national governments and security regimes.
7. Promoting digital etiquettes: such as culture of verification of social media messages, limiting spread of unverified messages and other media by masses among others.
8. TK Viswanathan committee: recommends amending IPC sections like section 153 and replacing some IT Act clauses. It also suggests that a state cyber coordinator and a district cyber crime cell be appointed.
IT Act, 2000

1. The Information Technology Act, 2000 (also known as ITA-2000, or the IT Act) is an Act of the Indian Parliament. It is the primary law in India dealing with cybercrime and electronic commerce.
2. Secondary or subordinate legislation to the IT Act includes the Intermediary Guidelines Rules 2011 and the Information Technology (Intermediary Guidelines and Digital Media Ethics Code) Rules, 2021.
3. The Act provides a legal framework for e-governance by giving recognition to electronic records and digital signatures. It also defines cyber crimes and prescribes penalties for them.
4. The Act directed the formation of a Controller of Certifying Authorities to regulate the issuance of digital signatures. It also established a Cyber Appellate Tribunal to resolve disputes rising from this new law.
Issues with IT Act, 2000
1. Right to Privacy not mentioned: Privacy is now a fundamental right in India, and being the primary law, the law needs to specifically address privacy concerns, but that is not the case in the IT Act, 2000.
2. Transparency issues: For example, Section 69A gives the government the authority to direct intermediaries to block access to any information it deems to be harmful to public order, national security, or India’s sovereignty and integrity.
3. Insufficient provisions for cybersecurity: The nuances of cybersecurity are not addressed in the Indian IT Act because it is not a cybersecurity law. The Cambridge Analytica breach, the Aadhaar account breach that affected 1.1 billion Indians, and the 2018 personal data leak that affected 5 lakh Google+ users are just a few examples of the numerous instances of data breaches and privacy violations that have affected Indian citizens.
4. Limited scope: The Act only covers electronic transactions and digital signatures, leaving out other important areas of e-commerce, such as online contracts and consumer protection.
5. Lack of international standards: The Act does not align with international standards on privacy and data protection, making it difficult for Indian companies to compete globally.
6. Censorship: The Act has been used to censor content on the internet, which has been criticized as being an infringement on freedom of speech and expression.
7. Lack of judicial oversight: The Act gives the government broad powers to intercept electronic communication, which can be abused without proper oversight.
Recent Steps taken
Information Technology (Intermediary Guidelines and Digital Media Ethics Code) Rules 2021
The Information Technology (Intermediary Guidelines and Digital Media Ethics Code) Rules 2021 were introduced by the Indian government to regulate digital media and social media platforms operating in India.
What was the need to amend the IT Rules, 2021?
1. As per the press note accompanying the draft amendments in June 2022, the stated objectives of the amendments were three-fold.
2. First, there was a need to ensure that the interests and constitutional rights of netizens are not being contravened by big tech platforms.
3. Second, to strengthen the grievance redressal framework in the Rules, and
4. third, that compliance with these should not impact early stage Indian start-ups.
5. This translated into a set of proposed amendments that can be broadly classified into two categories.
6. The first category involved placing additional obligations on the SMIs to ensure better protection of user interests while the second category involved the institution of an appellate mechanism for grievance redressal.
Key provisions of new IT rules are:
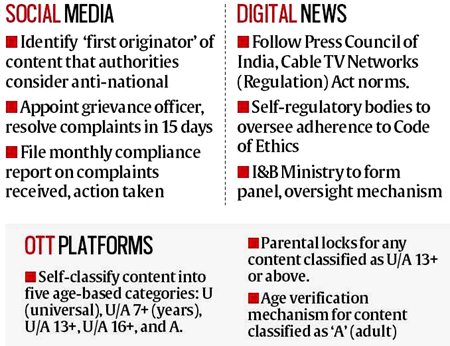
1. Appointment of Grievance Officer: The rules mandate that social media platforms and messaging apps with over 50 lakh users in India appoint a Grievance Officer who shall acknowledge complaints within 24 hours and resolve them within 15 days.
2. Removal of Content: The rules require social media platforms to remove certain types of content within 24 hours of receiving a complaint or a government order. This includes content that is defamatory, obscene, or infringes copyright.
3. Traceability of Content: The rules mandate social media platforms to provide information on the originator of a message or content when required by a court order or authorized government agency.
4. Self-Regulation Mechanism: The rules provide for a self-regulatory mechanism for over-the-top (OTT) platforms and digital news media. This includes a three-tier grievance redressal mechanism consisting of a self-regulatory body, an intermediary body, and an oversight mechanism.
5. Compliance Reports: The rules require social media platforms and messaging apps to publish compliance reports every six months, disclosing the number of complaints received, actions taken, and details of content removed.
6. User Verification: The rules require social media platforms to provide a mechanism for voluntary user verification, and social media intermediaries have to inform users once a month to provide them with the option to verify their accounts.
7. Content Classification: OTT platforms have to classify their content into five categories – U (Universal), U/A 7+, U/A 13+, U/A 16+, and A (Adult). Platforms also have to display the classification rating and content description before the start of any programme.

Issues with the new IT rules, 2021
1. Cumbersome three-tier regulatory structure: The rules restrict free speech by requiring OTT services and digital news publishers to adhere to a cumbersome three-tier regulatory structure. At its highest point, it has a government committee. This is unprecedented in a nation where the news media have always had the freedom to regulate themselves.
2. Platforms for social media: The new regulations have also made it harder for platforms for social media to comply. A court order will require these messaging platforms to “enable the identification of the first originator of the information on its computer resource.” Because these apps encrypt messages from beginning to end, it raises concerns.
3. High degree of Regulation: Anyone who has a complaint about content published by a publisher that violates the Code of Ethics may submit their complaint. As a result, a digital platform could be made to address any issue by virtually anyone. As a result, these organizations must comply with the regulations. Also, the Standards permit government to impact the arrangement of board individuals in the more elevated level administrative bodies.
4. Unfair Classification: OTT platforms and digital news media have been unfairly and arbitrarily lumped together and governed in the same way. Additionally, the IT Act of 2000 has been expanded to include digital news media in its regulatory scope without legislative intervention.
Way Forward
More data sharing could be counterproductive in a nation where the residents actually don’t have an data protection regulation to monitor themselves against overabundances committed by any party. In light of this, the personal data protection bill must be passed as soon as possible.
After that, under Section 69A of the IT Act, if regulation is still deemed necessary, it must be implemented through legislation that is debated in Parliament rather than relying on executive rule-making powers.





